Defending your organisation’s domains, endpoints, networks, files and users, Cynet 360 is the first platform to converge multiple security technologies with a 24/7 cyber SWAT team,
Offering automated detection and response for any type of threat. Cynet 360 is a real breakthrough in IT security .
Finds unknown threats, detects and remediates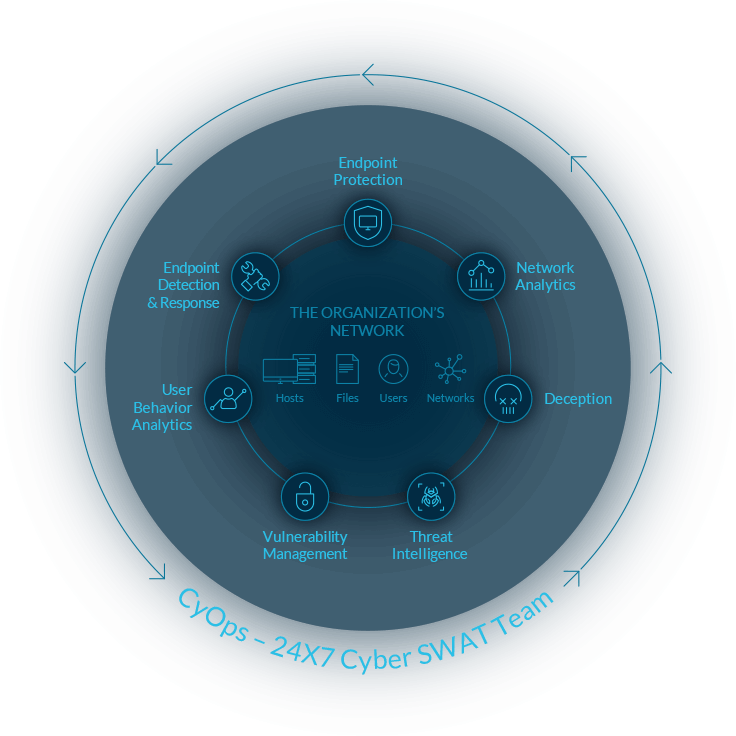
Cynet has a unique approach to threat detection, analysing and correlating indicators across networks, endpoints, files and users. Cynet integrates with any existing security infrastructure, providing organisations with rapid, flexible ability to respond – neutralising any unknown threats, anomalies and unsigned malware which have bypassed existing detection solutions.
Files
Cynet analyzes files for threats that bypass the security perimeter, infiltrating corporate systems and data files.
Networks
Cynet shows network attacks such as botnets and malicious IP addresses, password-based attacks, modification of network and server configurations, Denial-of-Service attacks and man-in-the-middle and compromised key attacks.
Users
Cynet monitors user activities to create a baseline of typical user behaviour including working hours, file access, server access and typical network traffic.
Endpoints
Cynet scans and monitors endpoints for indicators of compromise that bypass prevention systems.
{tab Key Features}
- All-in-one security platform
- Deployed in minutes
- Full visibility throughout the organisation
- Full 24/7 monitoring
- Very easy to use
- Automated detection and response for any type of threat
- Reduce time to detect and respond by built-in correlation
- Minimises false positives through correlation and risk scoring
{tab Videos}
{tab Docs}
{tab Licensing}
Very simple... Cynet 360 is licensed per user/mailbox
{tab System Requirements}
There are no real requirements over and above any standard infrastructure..
{/tabs}
