EgoSecure dos more than just blindly protect your data. Firstly, this unique solution determines the data protection situation of your network. It then gives you specific to your network, accurate information with guidance on how to protect yourself via the 20+ protection modules. This process can also be automated.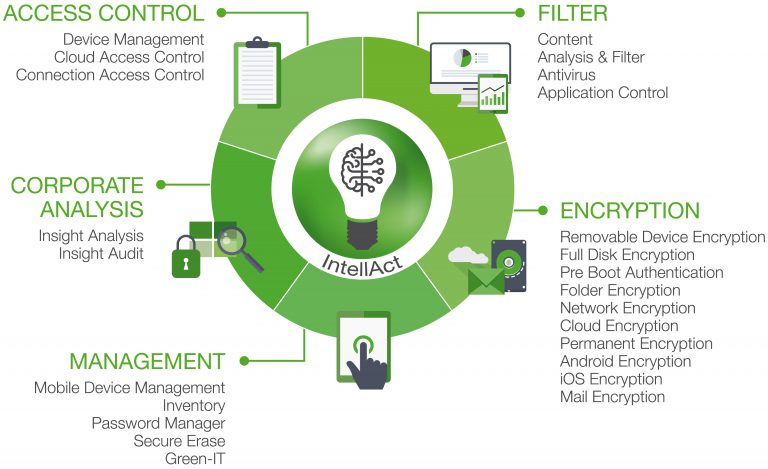
Data is the life-blood of every organisation and for more than 10 years, EgoSecure have been innovating and leading the way in the field of data protection. To date, more than 2,100 customers from every industry and of all sizes, are benefiting from EgoSecure Data Protection.
If data is lost due to theft, negligence or accident, it can ruin businesses and reputations. The most vulnerable points of attack are our devices, e.g. computers, smartphones, laptops, etc., which are operated by people – and people are fallible.
Firewall and Anti-virus protection are not enough to protect data.
EgoSecure Functions
After analyzing the data flow and identifying the weak links with Insight & IntellAct, the protective measures can be configured individually with 20 protective functions. These protective functions are based on the C.A.F.E. MANAGEMENT PRINCIPLE.
All functions are integrated into one solution, access only one database and are controlled via a central management console. There is only one installation, after which the functions can be activated in accordance with the protection requirements. A subsequent adjustment of the protection needs requires no new installation.
{tab Key Features}
- Corporate Analysis
INSIGHT-Audit
Audit makes the data flow visible in detail, showing potential weaknesses in the security settings. It therefore allows the determination of forensic information. The ability to generate this information is an important contribution to IT compliance and matches with laws and industry regulations. The Federal Data Protection Act, for example, specifies a logging as mandatory. At the same time EgoSecure INSIGHT-Audit makes the violation of the privacy rights of employees impossible, since the access to logging data is protected by a 4 or 6 eye principle.
INSIGHT-Analysis
To make sure that protective measures are implemented optimally, the INSIGHT module first determines the user’s overall safety situation in the corporate network.The results of this analysis are then processed according to management needs and shown in graphs and tables. Thus INSIGHT provides the facts to show an overall picture of the data security for every business and organization. The display is cumulative, so that conclusions about the activities of individual users are not possible. The data shown this way are optimal to specifically establish the protective measures that are really needed. - Access Control
Device Management
Device management allows a clear definition of who can use which devices (e.g. USB sticks, CDs, TV tuner) or interfaces (e.g. WLAN, Firewire, USB) and to what extent. Thus, all of these devices can be used without causing abuse or risking the loss of data. It also prevents malware of getting into the corporate network via these interfaces. Device Management offers effective protection against “attackers from inside”.
Cloud Access Control
The use of the cloud has many advantages in terms of flexibility of labour, because data can be accessed anywhere. Particularly sensitive data, however, should not be saved in the cloud and some data types may not even be allowed by law to be saved. Especially in so-called third countries. Cloud Access Control checks which employee is allowed to use which cloud services to which extent.
Connection Access Control
Data transfers are nowadays, in addition to the official channels via the corporate network, possible through many ways – Bluetooth, WiFi, modem, etc. However, a company should control via which routes data leave the company. Connection Access Control checks which employee has access to which data transmission devices. - Filter
Content Analysis & Filter
An integrated, overall security concept also has to provide options to analyse content, filter sensitive information that leaves the company and block damaged information within incoming data. Our Content Analysis & Filter provides granular and reliable protection of corporate data communications without affecting users‘ workflows and desired data transfers.
Antivirus
An antivirus solution provides proven protection against anonymous attackers from the internet. It is important to ensure a high detection rate to be able to respond quickly to new viruses and trojans. EgoSecure Data Protection integrates a leading-edge solution with an acknowledged high detection rate.
Application Control
Application Control allows configuration as to which user is allowed to start which programs. For instance, to prevent games or unlicensed software products being used. This way liability risks and economic damage can be avoided. It is also possible to block most viruses before antivirus solutions detect them. - Encryption
Removable Device Encryption
Mobile media such as USB sticks are important means to support increasingly flexible business and working environments. While devices are shrinking in size and increasing in performance, they are also lost or stolen more easily. Removable Device Encryption ensures that the data cannot be used by unauthorized parties. Password-based encryption and decryption can be achieved on any Windows computer, with full transparency for authorized users. Encryption is file-based, and various encryption types are available (for the whole company, for individual users or for certain user groups). It is possible to use multiple encryption types for one medium.
Full Disk Encryption
Full Disk Encryption provides comprehensive protection of all devices and encrypts the complete hard disk or partitions on the sector level. The solution also provides on-demand pre-boot authentication to authenticate users before the operating system is started. Automatic detection of new hard disks in the integrated encryption chip, lightning- fast initial encryption and the centralized management ensure the seamless integration with existing IT infrastructures.
Pre-Boot Authentication
Pre-Boot Authentication ensures that registration at Windows and related encryptions, such as the disk encryption, cannot be manipulated and circumvented by converting the hard drives, starting of USB / CD or the replacement of the operating system. The registration to the corresponding terminal will thereby take place immediately after the BIOS loading process, but before the start of the operating system. Besides passwords also many smart cards are supported as login security. Enterprise features such as help desk, self-initialization and more, are also available. Login screens can be customized to each customer.
Folder Encryption
Folder Encryption protects data on lost notebooks or hard drives and also secures individually defined sensitive data on systems that can be accessed by multiple users. For instance, highly sensitive management data can be protected against access through employees with many privileges, such as IT staff.
Cloud / Network Encryption
Cloud and Network Encryption can be used to encrypt folders in the cloud or on any network. Encryption keys remain within the company and are never stored in the cloud – a clear advantage over encryption solutions provided by cloud storage providers themselves.
Permanent Encryption (included in version 12)
Permanent Encryption encrypts files, no matter on which data carriers they are stored. These encrypted data packets also remain encrypted during the transfer to other data carriers. Thus, an encrypted file can be copied into an e-mail attachment or uploaded to a web-based cloud while being permanently encrypted. On external computers and mobile devices, the file can be opened by entering a password or by using a PKI token.
Android / iOS Encryption
The encryption for iOS and Android devices offers file-based protection on internal storages,memory cards and cloud accounts of mobile devices via app. Files are decrypted by entering a password.
Mail Encryption
Mail Encryption ensures the safe exchange of e-mails. For this purpose, no software needs to be installed on the receiving or transmitting system. Encrypted e-mails with an electronic signature can be sent and read within the user’s familiar environment. It is also easy to encrypt and transport large e-mails. - Management
Mobile Device Management
The increasing degree of adoption of mobile devices such as tablets and smartphones must also be reflected in corporate security architectures. Mobile Device Management ensures the intelligent integration of mobile devices, including support of the Android and iOS operating systems.
Inventory
With INVENTORY can be seen which hardware and software products are installed on the computers in the corporate network. However, the functions in INVENTORY that allow to see changes and to analyze those and also to be alerted if something changes, are much more important. The condition of the hardware can be displayed and reliably indicate any problems.
Password Manager (included in version 12)
Employees no longer have to write down their passwords and logins on Post-It’s or in word files – this task is now taken over by the secure Password Manager. Even when creating complex passwords, the password manager can support through an intelligent process. It is also possible to exchange logon information with colleagues by storing the protected Password Manager files in the network.
Secure Erase
Secure Erase ensures that deleted files cannot be restored, no matter if they are located on the internal hard disk or on an external storage medium. Users can choose among multiple deletion methods. They have the option to securely delete documents immediately or to destroy all deleted files irrevocably, based on a specific schedule. Secure Erase also ensures that you discard hardware only when you sell or withdraw respective hardware.
Green-IT
Intelligent power management ensures efficient device operations by ensuring that energy is only consumed when the computer is actually used. Power Management helps to reduce IT operational costs while also contributing to the company’s environmental balance and ensuring a fast ROI for the EgoSecure Data Protection implementation.
{tab Docs}
{tab Licensing}
License model EgoSecure Endpoint :
Purchase licensing or subscription agreement.
Module licensing on user, computer, or mobile device – level.
Licensing is done according to the named user license model.
Number of licenses to be calculated based on managed objects (user / computer)
License is released if it is disabled or deleted.
No additional licensing costs for installing server or client component.
{tab Screenshots}
{tab System Requirements}
On the server´s side it depends on the number of agents, but the following resources are required in normal operation:
Server
RAM: 100 MB
HDD: 5 GB
Client
RAM: 200 MB
HDD: 500 MB
{/tabs}

